Wired networks. Organization of networks. Wired and wireless data transmission. Development of wireless networks
Send your good work in the knowledge base is simple. Use the form below
Students, graduate students, young scientists who use the knowledge base in their studies and work will be very grateful to you.
Similar Documents
Research and analysis of wireless data transmission networks. Wireless connection technology wi-fi. Bluetooth short range radio technology. Bandwidth of wireless networks. Alternative routing algorithms in wireless networks.
term paper, added 01/19/2015
The evolution of wireless networks. Description of several leading network technologies. Their advantages and problems. Classification of wireless communications by range. The most common wireless data networks, their principle of operation.
abstract, added 10/14/2014
Problems and applications of wireless local networks. Physical layers and topologies of local area networks of the 802.11 standard. Improved OFDM coding and dual frequency channels. Benefits of using MIMO technology (multiple inputs and outputs).
test, added 01/19/2014
The principle of operation of wireless networks and devices, their vulnerability and main threats. Means of protection of information of wireless networks; WEP, WPA and WPA-PSK modes. Setting up network security when using intrusion detection systems using Kismet as an example.
term paper, added 12/28/2017
General concepts of wireless local networks, the study of their characteristics and main classifications. Application of wireless communication lines. Advantages of wireless communications. Ranges of the electromagnetic spectrum, propagation of electromagnetic waves.
term paper, added 06/18/2014
The main advantages obtained by networking personal computers in the form of an intra-industrial computer network. Methods for evaluating the effectiveness of local computer networks. Types of building networks by methods of information transfer.
abstract, added 10/19/2014
The history of the appearance of cellular communication, its principle of operation and functions. How Wi-Fi works is a trademark of the Wi-Fi Alliance for wireless networks based on the IEEE 802.11 standard. Functional diagram of a cellular mobile communication network. Advantages and disadvantages of the network.
abstract, added 05/15/2015
General concepts and basic aspects of building wireless local networks, features of their structure, interface and access points. IEEE 802.11 and HyperLAN/2 description of the media access control protocol. The main goals of the Wi-Fi alliance.
term paper, added 11/29/2011
Chelyabinsk
Introduction………………………………………………………………. 3
Chapter I. Wired LANs…………………………………….6
1.1 Types and topologies of local networks……………………………...6
1.2 Technologies used to build wired LANs……..7
1.3 Devices for creating local networks……...………….…..11
1.4 Wired LAN Security……...………….…..15
Chapter II. Wireless LANs….……………………………18 2.1 Basic properties of wireless LANs………………18
2.2 Topology of wireless computer networks...……………...19
2.3 Devices for creating wireless networks…………………21
2.4 Access method used in wireless communication………23
2.4 Wireless Security………..……...………….…..27
Conclusion……………………………………………………………29
References…………………………………………………...31
Introduction.
A computer network is a set of nodes (computers, terminals, peripheral devices) that have the ability to interact with each other using special communication equipment and software.
The sizes of networks vary widely - from a pair of interconnected computers standing on adjacent tables to millions of computers scattered around the world (some of them may be located on space objects).
According to the breadth of coverage, it is customary to divide networks into several categories: local area networks - LAN or LAN (Local-Area Network), allow you to combine computers located in a limited space.
For local networks, as a rule, a specialized cable system is laid, and the position of possible connection points for subscribers is limited by this cable system. Sometimes local networks use wireless communication (Wireless) but at the same time, the ability to move subscribers is very limited. Local networks can be combined into large-scale formations:
CAN (campus- area network) - a campus network that combines local networks of closely located buildings;
MAN (Metropolitan-Area Network)- urban scale network;
WAN (Wide-Area Network)- large-scale network;
GAN (Global-Area Network)- global network.
The network of networks in our time is called the global network - the Internet.
For larger networks, dedicated wired and wireless links are installed or existing public communications infrastructure is used. In the latter case, computer network subscribers can connect to the network at relatively arbitrary points covered by a telephony or cable television network.
Networks use different network technologies. Each technology has its own types of equipment.
Network equipment is divided into active - computer interface cards, repeaters, hubs, etc. and passive - cables, connectors, patch panels, etc. In addition, there are auxiliary equipment - uninterruptible power supplies, air conditioning and accessories - mounting racks, cabinets, cable conduits of various types. In terms of physics, active equipment is a device that needs power to generate signals, passive equipment does not require power.
Computer network equipment is divided into end systems (devices) that are sources and / or consumers of information, and intermediate systems that ensure the passage of information over the network.
End systems include computers, terminals, network printers, fax machines, cash registers, barcode readers, voice and video communications, and any other peripheral devices.
Intermediate systems include hubs (repeaters, bridges, switches), routers, modems and other telecommunications devices, as well as the cable or wireless infrastructure connecting them.
The action "useful" for the user is the exchange of information between end devices.
For active communication equipment, the concept of performance is applicable, and in two different aspects. In addition to the “gross” amount of unstructured information transmitted by equipment per unit of time (bit / s), they are also interested in the speed of processing packets, frames or cells. Naturally, the size of structures (packets, frames, cells) is also specified, for which the processing speed is measured. Ideally, the performance of communication equipment should be so high that it can process information falling on all interfaces (ports) at their full speed. (wire speed).
To organize the exchange of information, a complex of software and hardware distributed over different network devices should be developed. At first, network developers and vendors tried to go their own way, solving the whole range of problems using their own set of protocols, programs, and equipment. However, the solutions of various vendors turned out to be incompatible with each other, which caused a lot of inconvenience for users who, for various reasons, were not satisfied with the set of features provided by only one of the vendors. With the development of technology and the expansion of the range of services provided, there is a need to decompose network tasks - breaking them into several interrelated subtasks with defining the rules of interaction between them.
The breakdown of the task and the standardization of protocols allows a large number of parties to solve it - software and hardware developers, manufacturers of auxiliary and communication equipment, bringing all these fruits of progress to the end user.
ChapterI. Wired LANs
1.1 Topology and types of local networks.
The topology (layout, configuration, structure) of a computer network is usually understood as the physical location of network computers relative to each other and the way they are connected by communication lines. It is important to note that the concept of topology refers primarily to local networks in which the structure of connections can be easily traced. In global networks, the structure of communications is usually hidden from users and is not very important, since each communication session can be carried out along its own path.
The topology determines the requirements for the equipment, the type of cable used, the acceptable and most convenient methods of managing the exchange, the reliability of operation, and the possibility of expanding the network. There are three basic network topologies:
Bus (bus) - all computers are connected in parallel to one communication line. Information from each computer is simultaneously transmitted to all other computers (Figure 1).
Figure 1. Bus network topology
Star (star) - there are two main types:
1) Active star - other peripheral computers are connected to one central computer, and each of them uses a separate communication line. Information from the peripheral computer is transmitted only to the central computer, from the central one - to one or more peripheral ones.
2) Passive star. At present, it is much more widespread than an active star. Suffice it to say that it is used in the most popular Ethernet network today (which will be discussed later). In the center of the network with this topology, not a computer is placed, but a special device - a switch or, as it is also called, a switch, which restores incoming signals and sends them directly to the recipient.
Ring (ring) - computers are sequentially combined into a ring.
The transmission of information in a ring is always carried out in only one direction. Each computer transmits information to only one computer following it in the chain, and receives information only from the previous one.
In practice, other topologies of local networks are often used, but most networks are focused on precisely three basic topologies.
Types of local networks
All modern local networks are divided into two types:
1) Peer-to-peer local networks - networks where all computers are equal: each of the computers can be both a server and a client. The user of each computer decides for himself what resources will be shared.
2) Local networks with centralized management (server local networks). In local networks with centralized management, the server provides interaction between workstations, performs the functions of storing public data, organizes access to this data and its transmission.
1.2 Technologies used to build local networks.
There are a large number of technologies: Ethernet, FDDI, Token Ring, ATM, UltraNet and others. We will start with the most widely used technology:
ethernet.
This technology was developed in 1973 by a research center in Palo Alto. Ethernet is a network architecture with shared media and broadcast transmission, i.e., a network packet is sent immediately to all nodes of a network segment. Therefore, to receive, the adapter must accept all signals, and only then discard unnecessary ones if they were not intended for it. The adapter listens on the network before it starts transmitting data. If someone is currently using the network, the adapter delays the transmission and continues listening. In Ethernet, a situation can occur when two network adapters, having detected "silence" in the network, begin to transmit data simultaneously. In this case, a failure occurs and the adapters start over again after a small, random amount of time.
Today, Ethernet provides three data transfer rates - 10 Mbps, 100 Mbps (Fast Ethernet) and 1000 Mbps (Gigabit Ethernet). There is also 1Base5 Ethernet (1 Mbps), but it is practically not used.
Transfer rate - 100 Mbps.
Topology - ring or hybrid (based on star topologies).
The maximum number of stations is 1000, the maximum distance is 45 km.
High reliability, throughput and allowable distances, on the one hand, and the high cost of equipment, on the other hand, limit the scope of FDDI by connecting fragments of local networks built using cheaper technologies.
A technology based on the principles of FDDI, but using twisted-pair copper as the transmission medium, is called CDDI. Although the cost of building a CDDI network is lower than FDDI, a very significant advantage is lost - large allowable distances.
token ring
Token Ring (token ring) - architecture of networks with a ring logical topology and a token passing access method.
In 1970, this technology was developed by IBM, and then became the basis of the IEEE 802.5 standard. When this standard is used, data is (logically) always transmitted sequentially from station to station in a ring, although the physical implementation of this standard is not a "ring" but a "star".
When using Token Ring, a packet (through the ring) is constantly circulating in the network, called a token. When receiving a packet, the station can hold it for some time or transmit further.
In the center of the "star" is MAU - a hub with connection ports for each node. For connection, special connectors are used to ensure the closure of the Token Ring ring even when the node is disconnected from the network.
Transmission medium - shielded or unshielded twisted pair.
The standard transfer rate is 4 Mbps, although 16 Mbps implementations exist.
There are several options for wiring networks based on Token Ring. The light version provides connection of up to 96 stations to 12 hubs with a maximum distance from the hub - 45 m. Fixed wiring provides connection of up to 260 stations and 33 hubs with a maximum distance between devices of up to 100 m, but when using fiber optic cables, the distance increases to 1 km.
The main advantage of Token Ring is the obviously limited node service time (unlike Ethernet), due to the deterministic access method and the possibility of priority control.
ATM (Asynchronous Transfer Mode) is a technology that provides the transmission of digital, voice and multimedia data over the same lines. The initial transfer rate was 155 Mbps, then 662 Mbps and up to 2.488 Gbps. ATM is used in both local and wide area networks.
Unlike traditional technologies used in local area networks, ATM is a connection-oriented technology. That is, before the transmission session, a virtual sender-receiver channel is established, which cannot be used by other stations. In traditional technologies, the connection is not established, and packets with the specified address are placed in the transmission medium. Multiple ATM virtual circuits can simultaneously coexist on the same physical circuit.
ATM has the following features:
Providing parallel transmission.
Work is always at a certain speed (the bandwidth of the virtual channel is fixed).
Use of fixed length packets (53 bytes).
Routing and error correction at the hardware level.
As a disadvantage, you can indicate the very high cost of equipment.
UltraNet
UltraNet was specially created and is used when working with supercomputers.
The technology is a hardware and software complex capable of providing information exchange rates between devices connected to it up to 1 Gbps and uses a star topology with a hub at the central point of the network.
UltraNet is characterized by rather complex physical implementation and high cost of equipment. The elements of the UltraNet network are network processors and channel adapters. Also, the network may include bridges and routers to connect it with networks built using other technologies (Ethernet, Token Ring).
Coaxial cable and optical fiber can be used as transmission medium. Hosts connected to UltraNet can be up to 30 km apart from each other. Connections over long distances are also possible by connecting via high-speed WAN links.
Network protocols
A network protocol is a set of rules that allows connection and data exchange between two or more devices connected to a network.
Protocol TCP/IP are the two lower-layer protocols that are the basis of communication on the Internet. The TCP (Transmission Control Protocol) protocol breaks the transmitted information into portions and enumerates all portions. Using IP (Internet Protocol), all parts are transmitted to the recipient. Next, using the TCP protocol, it is checked whether all parts have been received. When all chunks are received, TCP arranges them in the right order and assembles them into a single whole.
The most famous protocols used on the Internet are:
http(Hyper Text Transfer Protocol) is a hypertext transfer protocol. The HTTP protocol is used to send Web pages from one computer to another.
FTP(File Transfer Protocol) is a protocol for transferring files from a special file server to a user's computer. FTP allows the subscriber to exchange binary and text files with any computer on the network. By establishing a connection with a remote computer, the user can copy a file from the remote computer to his own or copy a file from his computer to the remote one.
POP(Post Office Protocol) is a standard mail connection protocol. POP servers handle incoming mail, and the POP protocol is designed to handle requests to receive mail from client mailers.
SMTP(Simple Mail Transfer Protocol) - a protocol that defines a set of rules for mail transfer. The SMTP server either returns an acknowledgment, an error message, or requests additional information.
TELNET is a remote access protocol. TELNET allows the subscriber to work on any computer on the Internet, as on his own, that is, run programs, change the operating mode, etc. In practice, the possibilities are limited by the access level that is set by the administrator of the remote machine.
DTN- a protocol for deep space communications designed to provide ultra-long-range space communications.
1.3 Devices for creating local networks.
It just so happens that network equipment has always kept itself apart. Other components (from among those that are not included in the mandatory set of the system unit) can be purchased separately, you can easily do without some. But with network devices - the picture is completely different, you need to purchase everything in the aggregate.
network fee.
A network card, also known as a network card, NIC (network interface controller) is a peripheral device that allows a computer to communicate with other network devices.
According to the constructive implementation, network cards are divided into:
Internal - separate boards inserted into a PCI, ISA or PCI-E slot;
External, connected via USB or PCMCIA interface, mainly used in laptops;
built into the motherboard.
On 10-Mbit NICs, 3 types of connectors are used to connect to the local network:
8P8C for twisted pair;
BNC connector for thin coaxial cable;
15-pin transceiver connector for thick coaxial cable.
These connectors can be present in different combinations, sometimes even all three at once, but at any given moment only one of them works.
On 100-megabit boards, only a twisted-pair connector is installed.
Next to the twisted pair connector, one or more information LEDs are installed to indicate the presence of a connection and the transfer of information.
Cable.
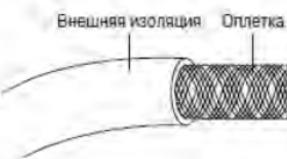
Obviously, cables are needed to connect different devices on a wired network. Naturally, not every cable can be used to connect network devices. Therefore, all network standards define the necessary conditions and characteristics of the cable used, such as bandwidth, characteristic impedance (impedance), specific signal attenuation, noise immunity, and others. There are two fundamentally different types of network cables: copper and fiber optic. Cables based on copper wires, in turn, are divided into coaxial and non-coaxial. The commonly used twisted pair (RG-45) does not formally refer to coaxial wires, but many of the characteristics inherent in coaxial wires apply to it.
Coaxial cable is a central conductor surrounded by a dielectric layer (insulator) and a metal braid screen, which also acts as a second contact in the cable. To improve noise immunity, sometimes a thin layer of aluminum foil is placed over the metal braid. The best coaxial cables use silver and even gold to make them. In local networks, cables with a resistance of 50 ohms (RG-11, RG-58) and 93 ohms (RG-62) are used. The main disadvantage of coaxial cables is their bandwidth, which does not exceed 10 Mbps, which is considered insufficient in modern networks.
twisted pair consists of several (usually 8) pairs of twisted conductors. Twisting is used to reduce interference from both the pair itself and external ones that affect it. A pair twisted in a certain way has such a characteristic as wave resistance. There are several types of twisted pair: unshielded twisted pair - UTP (Unscreened Twisted Pair), foil - FTP (foiled), foil shielded - FBTP (foiled braided) and protected - STP (shielded). The protected pair differs from the others in the presence of an individual screen for each couples. Twisted pairs are categorized according to their frequency properties. Depending on where the wire is laid and what its further use is, you should choose a single-core or multi-core twisted pair. A single-core pair is cheaper, but it is the most fragile.
Fiber optic cable consists of one or more fibers enclosed in jackets, and comes in two types: single-mode and multi-mode. Their difference is in how light propagates in the fiber - in a single-mode cable, all rays (sent at the same time) travel the same distance and reach the receiver at the same time, and in a multimode cable, the signal can be "smeared". But they are much cheaper than single-mode ones.
The advantages of a fiber optic cable relative to copper are the insensitivity of the first to electromagnetic interference, a higher data transfer rate due to a much larger bandwidth (optical frequencies are much higher than the frequencies of electromagnetic waves in a conductor) and the difficulty in intercepting information. It is easier to intercept electromagnetic radiation than optical radiation, although optics is not a panacea. But on the other hand, for the same reason, copper wires can be easily connected and mounted (if the cable lengths are not close to critical), and special equipment is required for the installation of a fiber optic cable, since it is necessary to accurately align the axes of the light-conducting material - fibers and connectors.
The Fast Ethernet network, built on the "star" technology, does not imply the direct connection of several computers to each other via a "common bus", as was the case in "coaxial" networks, but their connection to a common distribution device - a hub.
These devices are of several types. The simplest ones are hubs
(hubs) ,
which are only able to “bundle” computers of one of the network segments, amplifying the signals of each of them and transmitting them to all other stations connected to the hub. The hub is suitable for the device of small networks consisting of several computers - or segments of large networks.
The main characteristic of a hub is the type and number of ports. The cheapest models are equipped with 5 or 8 ports - and these are the devices you should choose to create a small network within the same floor. More powerful devices already support 16 or more ports, but they are much more expensive.
Most modern hubs are manufactured to work with a twisted pair network. In addition to hubs, there are more complex and intelligent devices switches(switch ) , or switches. Unlike hubs, a switch is capable of not only sending an incoming signal to all ports at once, but also sorting network information on its own. In a local network, a switch is a post office: it determines which computer a particular packet is addressed to and delivers it exactly to its destination.
Router (router)
A router is a network device that, based on information about the network topology and certain rules, makes decisions about forwarding network layer packets between different network segments. Typically, the router uses the destination address specified in the data packets and determines from the routing table the path over which the data should be sent. If there is no described route in the routing table for the address, the packet is dropped. .
1.4 Wired LAN Security
The transition from working on personal computers to working on a network complicates the protection of information for the following reasons:
A large number of users in the network and their variable composition. Security at the level of user name and password is not sufficient to prevent unauthorized persons from entering the network;
Significant length of the network and the presence of many potential channels of penetration into the network;
Deficiencies in hardware and software, which are often discovered not at the pre-sale stage, called beta testing, but during operation. Including the built-in means of protecting information, even in such well-known and network operating systems as Windows NT or NetWare, are not ideal.
The severity of the problem associated with a large network length for one of its segments on a coaxial cable is illustrated in Figure 2. There are many physical places and channels of unauthorized access to information in the network in the network. Every device on the network is a potential source of electromagnetic radiation (with the exception of fiber optics) due to the fact that the corresponding fields, especially at high frequencies, are not ideally shielded. The grounding system, together with the cable system and the power supply network, can serve as a channel for accessing information in the network, including in areas that are outside the zone of controlled access and therefore are especially vulnerable. In addition to electromagnetic radiation, non-contact electromagnetic effects on the cable system are a potential threat. Of course, in the case of using wired connections such as coaxial cables or twisted pairs, a direct physical connection to the cable system is also possible. If passwords for logging into the network become known or hacked, it becomes possible to gain unauthorized access to the network from a file server or from one of the workstations. Finally, information can be leaked through channels outside the network:
storage media,
Elements of building structures and windows of premises that form channels for the leakage of confidential information due to the so-called microphone effect,
Telephone, radio, and other wired and wireless channels (including mobile communication channels).
Figure 2. Places and channels of possible unauthorized access to information in a computer network
Any additional connections to other segments or connection to the Internet creates new problems. Attacks on a local network through an Internet connection in order to gain access to confidential information have recently become widespread, due to the shortcomings of the built-in protection system. Network attacks over the Internet can be classified as follows:
Packet sniffer (sniffer - in this case in the sense of filtering) is an application program that uses a network card operating in promiscuous (does not distinguish) mode (in this mode, all packets received over physical channels are sent by the network adapter to the application for processing) .
IP spoofing (spoof - deception, hoax) - occurs when a hacker, either inside or outside a corporation, impersonates an authorized user.
Denial of Service (DoS). A DoS attack renders a network unavailable for normal use by exceeding the allowable limits of the network, operating system, or application.
Password attacks - an attempt to guess the password of a legal user to enter the network.
Man-in-the-Middle attacks - direct access to packets transmitted over the network.
Application layer attacks.
Network intelligence - gathering information about the network using publicly available data and applications.
Abuse of trust within the network.
Unauthorized access, which cannot be considered a separate type of attack, since most network attacks are carried out in order to gain unauthorized access.
Viruses and Trojan horse applications.
ChapterII. Wireless LANs.
2.1 Basic properties
Wireless data networks (WDNs) allow you to combine disparate local networks and computers into a single information system to provide access for all users of these networks to common information resources without laying additional wired communication lines.
BSPDs are usually created in cases where the installation of a cable system is difficult or not economically feasible. An example is enterprises with a distributed structure (warehouses, separate workshops, quarries, etc.), the presence of natural barriers in the construction of cable systems (rivers, lakes, etc.), enterprises renting offices for a short period, exhibition complexes, etc. hotels that provide Internet access for their customers .
Wireless LANs reduce the cost of space planning and preparation, hardware upgrades and peripherals, while providing a small range of mobility for laptop and PDA users.
The most popular wireless networks schemes:
WiFi(eng. Wireless Fidelity - “wireless accuracy”) - a standard for Wireless LAN equipment. The installation of Wireless LAN was recommended where deployment of a cable system was not possible or not economically viable. At the present time, many organizations use Wi-Fi, since under certain conditions the network speed already exceeds 100 Mbps. Users can move between access points within the Wi-Fi coverage area. Mobile devices (PDAs, smartphones, PSPs and laptops) equipped with client Wi-Fi transceivers can connect to a local network and access the Internet through access points.
WiMAX(Eng. Worldwide Interoperability for Microwave Access) is a telecommunications technology designed to provide universal wireless communication over long distances for a wide range of devices (from workstations and laptops to mobile phones). Based on the IEEE 802.16 standard, also called Wireless MAN.
WiMAX is suitable for the following tasks:
Connections of Wi-Fi access points with each other and other segments of the Internet.
Providing wireless broadband access as an alternative to leased lines and DSL.
Provision of high-speed data transmission and telecommunication services.
Creation of access points that are not tied to a geographic location.
WiMAX allows you to access the Internet at high speeds, with much greater coverage than Wi-Fi networks. This allows the technology to be used as “backbone channels”, which are continued by traditional DSL and leased lines, as well as local networks. As a result, this approach allows you to create scalable high-speed networks across entire cities.
Bluetooth
Bluetooth - a production specification for wireless personal area networks (WPAN), provides information exchange between devices such as pocket and ordinary personal computers, mobile phones, laptops, printers, digital cameras, mice, keyboards, joysticks, headphones, headsets on a reliable, low-cost, ubiquitous short-range radio frequency. Bluetooth allows these devices to communicate when they are within a radius of 10-100 meters from each other (the range is very dependent on obstacles and interference), even in different rooms.
2.2 Topology of wireless computer networks
There are two main areas of application of wireless computer networks - work in a closed volume (office, showroom, etc.) and connection of remote local networks (or remote segments of a local network).
To organize a wireless network in a confined space, transmitters with omnidirectional antennas are used. The IEEE 802.11 standard defines two modes of network operation - Ad-hoc and client/server. Ad-hoc mode (otherwise called "point-to-point") is a simple network in which communication between stations (clients) is established directly, without the use of a special access point. In client/server mode, a wireless network consists of at least one access point connected to a wired network and a set of wireless client stations. Because most networks require access to file servers, printers, and other devices connected to a wired LAN, the client/server mode is most commonly used. Without connecting an additional antenna, stable communication for IEEE 802.11b equipment is achieved on average at the following distances: open space - 500 m, a room separated by non-metallic material partitions - 100 m, a multi-room office - 30 m. Please note that through walls with a high content of metal reinforcement (in reinforced concrete buildings, these are load-bearing walls), 2.4 GHz radio waves sometimes may not pass at all, so you will have to set up your own access points in rooms separated by such a wall. To connect remote local networks (or remote segments of a local network), equipment with directional antennas is used, which makes it possible to increase the communication range up to 20 km (and up to 50 km when using special amplifiers and high antenna heights). Moreover, Wi-Fi devices can also act as such equipment, you just need to add special antennas to them (of course, if this is allowed by the design). Complexes for connecting local networks according to topology are divided into "point-to-point" and "star". With a point-to-point topology (Ad-hoc mode in IEEE 802.11), a radio bridge is organized between two remote network segments. With a star topology, one of the stations is central and interacts with other remote stations. In this case, the central station has an omnidirectional antenna, and the other remote stations have unidirectional antennas. The use of an omnidirectional antenna in the central station limits the communication range to about 7 km. Therefore, if you want to connect segments of a local network that are more than 7 km apart from each other, you have to connect them on a point-to-point basis. In this case, a wireless network is organized with a ring or other, more complex topology.
2.3 Devices for creating wireless computer networks.
Most adapters for wireless computer networks are now available in the PC Card Type II card format, which provides for installing the device in a laptop, although there are adapter models for installing in PCI or ISA slots, but there are much fewer of them. Therefore, alas, to install a wireless network adapter in a desktop personal computer, you also have to purchase an additional adapter inserted into the PCI slot. Relatively recently, the production of Wi-Fi network adapters made in the form of CompactFlash standard cards has begun. Such devices are designed for pocket computers running under the operating system Windows CE (Pocket PC). There are also Wi-Fi network adapters made as separate devices with a USB interface.
The current trend is to use internal antennas in network adapters. In access points, external antennas are more often used to increase the communication range. Some access point models use the same network adapter as the client station as a transceiver, and it is just as easy to replace it in the access point as in the client station. Such a technical solution limits the communication range (and a long range for an apartment or a small office may turn out to be unnecessary), and the reason that prompted the engineers to take such a step is not entirely clear. Perhaps they thought that it would be easier to upgrade the access point if any changes were made to the wireless networking standard at the physical layer.
Figure 3 3Com AirConnect Network Adapter
A typical case is the combination of an access point and a router in one device. The access point may also include some other devices, such as a modem. For a small office, it is very convenient to use an access point combined with a print server. You can connect the most ordinary printer to it, thereby turning it into a network one.
Access point management in modern wireless networks, as a rule, is carried out using the TCP / IP protocol through a regular Internet browser.
It is clear that client stations are still much more expensive than simple Ethernet network cards. But what matters is not the cost of client devices as such, but the total cost of the system, as well as its installation and maintenance. And here we are faced with a new situation: the difference between the cost of a set of equipment for a wired Ethernet network (including the cost of buying a cable) and the cost of a set of IEEE 802.11b equipment is comparable in order of magnitude to the cost of laying a cable. And if the downward trend in prices for wireless network equipment continues (despite the fact that the cost of laying a cable depends significantly on the cost of labor, which is currently growing in our country), then in the near future it may turn out that in some cases it is more economically profitable to deploy a wireless local area network, than messing around with cabling.
2.4 Access method used in wireless communications.
IEEE 802.11 standard for wireless access
The IEEE 802 Standards Committee formed the 802.11 Wireless LAN Standards Working Group in 1990. This group was engaged in the development of a universal standard for radio equipment and networks operating at a frequency of 2.4 GHz, with access speeds of 1 and 2 Mbps (Megabits-per-second). Work on the creation of the standard was completed after 7 years, and in June 1997 the first 802.11 specification was ratified. The IEEE 802.11 standard was the first standard for WLAN products from an independent international organization that develops most of the standards for wired networks. However, by that time, the initial data transfer rate in the wireless network no longer met the needs of users. In order to make Wireless LAN technology popular, cheap, and most importantly, satisfy today's stringent requirements of business applications, developers were forced to create a new standard.
In September 1999, the IEEE ratified an extension to the previous standard. Called IEEE 802.11b (also known as 802.11 High rate), it defines a standard for wireless networking products that operate at 11 Mbps (similar to Ethernet), making these devices successful in large organizations. Compatibility between products from different manufacturers is guaranteed by an independent organization called the Wireless Ethernet Compatibility Alliance (WECA). This organization was created by the leaders of the wireless communications industry in 1999. Currently, more than 80 companies are members of WECA, including such well-known manufacturers as Cisco, Lucent, 3Com, IBM, Intel, Apple, Compaq, Dell, Fujitsu, Siemens, Sony, AMD, etc.
IEEE 802.11 standard and its 802.11b extension
Like all IEEE 802 standards, 802.11 operates on the lower two layers of the ISO/OSI model, the physical layer and the data link layer (Figure 3). Any network application, network operating system, or protocol (such as TCP/IP) will work just as well on an 802.11 network as it does on an Ethernet network.
Figure 3. Layers of the ISO/OSI model and their compliance with the 802.11 standard.
The basic architecture, features, and services of 802.11b are defined in the original 802.11 standard. The 802.11b specification only affects the physical layer, adding only higher access rates.
802.11 operating modes
802.11 defines two types of hardware - a client, which is usually a computer equipped with a wireless network interface card (Network Interface Card, NIC), and an access point (AP), which acts as a bridge between wireless and wired networks. An access point usually contains a transceiver, a wired network interface (802.3), and data processing software. The wireless station can be an ISA, PCI or PC Card network card in the 802.11 standard, or built-in solutions, such as a telephone headset. 802.11.
The IEEE 802.11 standard defines two modes of network operation - "Ad-hoc" mode and client/server (or infrastructure mode). In client/server mode, a wireless network consists of at least one access point connected to a wired network and a set of wireless end stations. This configuration is called the Basic Service Set (BSS). Two or more BSSs forming a single subnet form an Extended Service Set (ESS). Since most wireless stations need to access file servers, printers, Internet available on a wired LAN, they will work in client/server mode.
Ad-hoc mode (also called point-to-point, or independent basic service set, IBSS) is a simple network in which communication between multiple stations is established directly, without the use of a special access point. This mode is useful if the wireless network infrastructure is not formed (for example, a hotel, exhibition hall, airport), or for some reason cannot be formed.
Figure 4. Architecture of the "Ad-hoc" network.
Physical layer 802.11
Channel (Data Link) layer 802.11
The 802.11 link layer consists of two sublayers: Logical Link Control (LLC) and Media Access Control (MAC). 802.11 uses LLC and 48-bit addressing like other 802 networks, which makes it easy to combine wireless and wired networks, but the MAC layer is fundamentally different.
The 802.11 MAC layer supports multiple users on a shared media when the user validates the media before accessing it. For 802.3 Ethernet networks, the Carrier Sence Multiple Access with Collision Detection (CSMA/CD) protocol is used, which defines how Ethernet stations access a wired line and how they detect and handle collisions that occur when multiple devices try to simultaneously establish network communication.
CSMA/CA works as follows. A station wishing to transmit tests the channel, and if no activity is detected, the station waits for some random amount of time and then transmits if the medium is still free. If the packet arrives intact, the receiving station sends an ACK packet, upon receipt of which the sender completes the transmission process. If the transmitting station did not receive an ACK packet, because no data packet was received, or a corrupted ACK arrived, it is assumed that a collision has occurred, and the data packet is transmitted again after a random period of time.
The Channel Clearance Algorithm (CCA) is used to determine if a channel is free. Its essence is to measure the signal energy at the antenna and determine the received signal strength (RSSI). If the received signal strength is below a certain threshold, then the channel is declared free, and the MAC layer receives the CTS status. If the power is above the threshold, data transmission is delayed according to protocol rules. The standard provides another feature for determining channel idleness, which can be used either alone or in conjunction with the RSSI measurement - the carrier test method. This method is more selective because it checks for the same carrier type as the 802.11 specification. The best method to use depends on the level of interference in the work area.
Thus, CSMA/CA provides a way to share access over the air. The explicit acknowledgment mechanism effectively solves interference problems. However, it adds some additional overhead that 802.3 does not, so 802.11 networks will always be slower than their equivalent Ethernet LANs.
Network connection
The MAC layer 802.11 is responsible for how a client connects to an access point. When an 802.11 client enters the range of one or more access points, it selects one of them and connects to it based on the signal strength and the observed value of the number of errors. As soon as the client receives an acknowledgment that it is accepted by the access point, it tunes into the radio channel in which it operates. From time to time, it checks all 802.11 channels to see if another access point is providing better service. If such an access point is located, then the station connects to it, retuning to its frequency.
A reconnect usually occurs if the station has been physically moved away from the access point, causing the signal to weaken. In other cases, the reconnection is due to a change in the RF characteristics of the building, or simply due to heavy network traffic through the original access point. In the latter case, this protocol feature is known as "load balancing", since its main purpose is to distribute the total load on the wireless network in the most efficient way possible across the entire network infrastructure available.
2.4 Wireless Security
IEEE 802.11 networks have certain measures in place to limit the number of clients that can connect to an access point. Each station is assigned a unique ESSID, which must be sent to the access point in order to connect to it. In addition, each access point can store a list of MAC addresses and connect only those clients that are mentioned in this list.
Encryption of transmitted information in IEEE 802.11 wireless computer networks is carried out according to the WEP (Wired Equivalent Privacy) standard, which is based on the RC4 algorithm with a key length of 40 or 64 bits. WEP is being replaced by the WEP2 standard with a key length of 128 bits. Support for WEP is a prerequisite for equipment to obtain Wi-Fi compliance certification, which ensures device compatibility when exchanging encrypted information. At the same time, equipment manufacturers are adding additional support for other encryption algorithms, such as LEAP with a key length of 128 bits.
The power emitted by the transmitter of the access point or client station operating under the IEEE 802.11b standard does not exceed 0.1 W. For comparison, the power emitted by a mobile phone is an order of magnitude greater. Since, unlike a mobile phone, network elements are located far from the head, in general, it can be considered that wireless computer networks are safer from the point of view of health than mobile phones.
If a wireless network is used to connect long-distance LAN segments, the antennas are typically placed outdoors and at high altitudes.
Conclusion
Wireless networks seem preferable to wired networks due to the following advantages:
- Mobility of users. The technology allows users to move within the coverage area of a wireless network without interrupting the use of network resources.
-Speed and ease of deployment. Unlike wired data transmission systems, wireless networks do not require cabling, which usually takes up most of the time when implementing wired networks.
-Flexibility. Rapid restructuring, changing the size and configuration of the network, connecting new users.
-Saving investments. Wireless networks are convenient to use if you need to deploy a network for a short period of time or there is a possibility of moving.
-Possibility of deployment where it is impossible to use cable networks: the presence of rivers, lakes, swamps, etc., the deployment of a network on the territory of architectural monuments.
But like any other complex technology, wireless computer networks have not only positive but also negative sides. One of the most important problems is the possible presence of obstacles in the path of radio waves, which must be taken into account when placing the access point and client stations. Metal structures can create signal reflections, creating the so-called. the effect of multipath reception, when several variants of the transmitted signal arrive at the antenna located on the receiving side, shifted in phase one relative to the other. Multipath reception greatly increases the error rate. Another problem is the "free status" of the 2.4 GHz band. It can operate, for example, microwave oven generators or medical devices. Information transmitted over a wireless network is relatively easy to intercept. Yes, now algorithms are used that can be "opened" by direct enumeration, except perhaps using a supercomputer. But the performance of computing technology is growing at a rapid pace. It is possible that in a few years the information security systems used in wireless computer networks can be hacked using a personal computer. But there is no hope that during this time the encryption algorithms allowed for mass use will be adequately improved, since the United States has put before the world the question of limiting the improvement of mass means of cryptographic protection of information.
Bibliography
1. V.I. Vasiliev et al. Methods and means of organizing data transmission channels.
2. Computers, systems and networks. Textbook edited by
A.V. Pyatibratova.
3. F. Jennings. Practical data transmission: modems, networks, protocols.
4. Y. Black. Computer networks: protocols, standards, interfaces.
5. http://ru.wikipedia.org/
Any signal is inextricably linked with a certain material system called communication system or information transfer system. Signal
a physical process is called (for example, a certain sequence of electrical impulses or electrical oscillations of certain frequencies) that uniquely corresponds to a given message. On fig. 70 shows a diagram of the transfer of information between the source and the recipient.
Rice. 70.
The ultimate goal of the system is to transfer a message from the source to the recipient. This goal must be considered achieved if the message received by the recipient IN matches the message exactly BUT. The transmitter converts the message into a transmitted signal. The rules by which a message is converted into a signal are different depending on the types of messages and signals (modulation, coding, manipulation).
Communication line or physical Environment, over which signals are transmitted may be a cable, i.e. a set of wires isolated from each other and located in a protective sheath, as well as the earth's atmosphere or outer space through which electromagnetic waves propagate. The same communication line can be used to implement one or more communication channels.
The received signal at the output of the communication channel differs from the input transmitted signal due to the imposition of interference on the useful signal. The receiver recovers the message transmitted by the information source from the received signal. This operation is possible if the rule for converting a message into a signal is known. Based on this rule, a rule is developed for the inverse transformation of a signal into a message (demodulation, decoding).
However, the communication system is under the influence interference(noise), which can distort the signals transmitted over the communication line, and the message can be received by the recipient with distortion.
Recipient in information transmission systems, it is either directly a person or technical means associated with a person.
When two or more computers are physically connected, a computer network. In general, the following elements are required to build a network:
- - physical (cable) or wireless (infrared or radio frequency) connection of computers;
- - a set of rules governing the format and procedures for the exchange of information between two or more independent computers is called protocol;
- - data communication equipment - a general term applied to hardware that provides a connection to a network, such as modems, transceivers, etc.;
- - software that can be used to distribute resources between other computers, called network operating system;
- - shared resources: printers, hard drives, CD-ROM, DVD-ROM drives, etc.;
- - software with which you can access shared resources, called client software.
Depending on the data transmission medium, the following communication lines are distinguished:
- - wire (air);
- - cable (copper and fiber-optic);
- - radio channels of terrestrial and satellite communications;
- - wireless.
Wired (overhead) communication lines are wires without any insulating or shielding braids, laid between poles and hanging in the air. Such communication lines traditionally carry telephone or telegraph signals, but in the absence of other possibilities, these lines are also used to transmit computer data. The speed qualities and noise immunity of these lines leave much to be desired. Today, wired communication lines are being replaced by cable ones.
Cable lines are a rather complex structure, consisting of conductors enclosed in several layers of insulation: electrical, electromagnetic, mechanical, climatic. In addition, the cable can be equipped with connectors that allow you to connect various equipment to it. Three main types of cable are used in computer networks: cables based on twisted pairs of copper wires, coaxial cables with a copper core (Fig. 71), and fiber optic cables.

Rice. 71.
A twisted pair of wires is called twisted pair. A twisted pair exists in a shielded version (Fig. 72), when a pair of copper wires is wrapped in an insulating shield, and unshielded, when there is no insulating wrap. Due to the twisting of the wires, the penetration of external electrical noise into the line during data transmission is reduced. A coaxial cable consists of an inner copper core and a braid separated from the core by a layer of insulation. There are several types of coaxial cable that differ in characteristics and applications - for local networks, for global networks, for cable television, etc.
Coaxial cable is made in two types: thick and thin. The first one provides more reliable protection against external interference, transmits information over long distances, but is expensive.

Rice. 72.
The second type of cable transmits information over short distances, but is cheaper and easier to connect.
fiber optic cable consists of thin (3-60 microns) fibers through which light signals propagate. This is the highest quality type of cable - it provides data transmission at a very high speed (up to 10 Gb / s and higher) and, moreover, better than other types of transmission medium, it provides data protection from external interference. The cable requires high-quality installation, is expensive to manufacture, difficult to install and maintain.
Radio channels of terrestrial and satellite communications generated by a transmitter and receiver of radio waves. There are a large number of different types of radio channels, differing both in the frequency range used and in the channel range. The ranges of short, medium and long waves (HF, MW and LW), also called amplitude modulation ranges, provide long-distance communication, but at a low data rate. More high-speed are the channels operating on the ranges of ultrashort waves, which are characterized by frequency modulation, as well as the ranges of microwave frequencies. In the microwave range (above 4 GHz), signals are no longer reflected by the Earth's ionosphere, and stable communication requires a line of sight between the transmitter and receiver. Therefore, such frequencies use either satellite channels or radio relay channels, where this condition is met.
Wireless networks serve as an alternative to traditional cable systems. The main difference from cable LAN systems is that data between individual computers and network devices is transmitted not through wires, but through a highly reliable wireless channel. Through the use of a wireless network built in accordance with the Wi-Fi standard (from the English. Wireless Fidelity - wireless precision), you can ensure the flexibility and scalability of the local network, the ability to easily connect new equipment, workplaces, mobile users, regardless of whether they are used whether laptop, netbook or traditional personal computer.
The use of wireless network technologies makes it possible to make a company more attractive in the eyes of customers by providing additional services, such as: Internet access in a conference room or meeting room, organization of a hot spot (Hot-spot) access, etc.
In computer networks today, almost all the described types of physical data transmission media are used, but the most promising are fiber-optic. Today, both backbones of large territorial networks and high-speed communication lines of local networks are being built on them. A popular medium is also twisted pair, which is characterized by an excellent ratio of quality and cost, as well as ease of installation. With the help of twisted pair, end subscribers of networks are usually connected at distances up to 100 meters from the hub. Satellite channels and radio communications are used most often in cases where cable communications cannot be used - for example, when passing the channel through a sparsely populated area or to communicate with a mobile network user.
- 1. What is called a signal? Draw a diagram of the transfer of information between the source and the recipient.
- 2. What is a communication line or physical medium?
- 3. When is a computer network formed? Name the elements needed to build a network.
- 4. What is called a protocol?
- 5. Give a description of wired communication lines.
- 6. What types of cables do you know? Describe each.
- 7. How are radio channels of terrestrial and satellite communications formed?
- 8. According to what standard are wireless networks built? What are the advantages of wireless networks? What data transmission media are the most promising?
Workshop
Modem. Data Rate Units
Modem is a device that converts digital signals to analog signals, which are then transmitted over a telephone line (this process is called modulation), and performing inverse conversion, in which analog signals are converted to digital (demodulation). Thus, the name "modem" comes from a combination of the words "modulation-demodulation".
Main characteristics of the modem
Transfer rate measured in bps To ensure an acceptable connection speed, the user's and ISP's modems must operate at 56 Kbps, which is the maximum capacity of a telephone line. You can sometimes hear that the data transfer rate is measured in bauds. This value indicates how many times per second the state of the signal transmitted from one computer to another changes. If the frequency of the signal changes 300 times per second, then the signal transmission rate is said to be 300 baud. However, if not one, but, for example, two bits are transmitted at each signal change, then the transmission rate will be 600 bps. Therefore, the baud rate is less than the bit/s data rate.
Protocol support V.92 (modulation). Previously, it was believed that the maximum data transfer rate over analog communication lines could not exceed 33.6 Kbps. This is the so-called Shannon's law, discovered in 1948. It determines the maximum data transfer rate in a communication channel based on its bandwidth and the degree of signal distortion caused by various noises.
Although most modems support 56Kbps data rates, you should keep in mind that data at this rate will be transferred from a digital automatic telephone exchange (PBX) to the user's computer. In the opposite direction - from the computer to the server, they will be transmitted at a speed of 33.6 Kbps.
The V.92 standard is a modern communication protocol supported by Internet Service Providers. V.92 protocol requires (but not sufficient) that the local telephone exchange, as well as the Internet service provider's PBX, be digital. Otherwise, connection via this protocol is impossible and the need to purchase a modem with support for this particular protocol does not make sense.
Compared to the previous V.90 standard, V.92 introduces three innovations:
- increase in data transfer rate.
The use of V.92 allows you to increase the maximum data transfer rate up to 48 Kbps. This is 40% faster than the 33.6 Kbps speed provided by the V.90 standard. Such a high transfer rate brings significant benefits in cases such as sending large emails with attached files, uploading information to an ftp server, and also allows you to improve performance with interactive applications such as online games;
- fast connection function.
Speed up connection reduces the time spent on connection with the Internet provider by saving the line parameters from the previous communication session in the modem's memory. In some cases, using Fast Link Setup can halve the time it takes to set up a connection, from 20 seconds with a V.90 modem to 10 seconds with a V.92 modem;
- a call hold feature that allows you to answer a call while the modem is busy on the line.
Call Hold allows you to answer a call while the modem is busy on the line. The user can answer the phone call and talk for the time allowed by the ISP without interrupting the modem connection. After the conversation ends, the modems will automatically continue communication and the user can resume his work with the Internet.
Support for V.42 error correction (correction) protocol. Under correction refers to the ability of modems to detect transmission errors and retransmit data that has been corrupted.
The functions of the V.42 protocol can be briefly described as follows: data received from a computer is divided into blocks of a fixed length - packets or "frames". Each packet is preceded by a start bit, which indicates the start of data transfer, and a stop bit, which indicates the end of the transfer. The receiving modem receives each of the frames in sequence, and in response to receiving the last frame sends a confirmation of successful reception. After receiving confirmation, the transmitting modem starts sending the next portion of data. If a packet was corrupted during a receive due to a random error, the receiving modem will send a request to retransmit the packet: this ensures data integrity during transmission.
The V.42 error correction protocol is compatible with MNP (Microcom Network Protocol). In particular, the MNP 10 protocol is designed to provide communication between wired and wireless communication systems such as cellular lines, long distance lines, rural lines. This is achieved using the following methods:
- - repeated attempts to establish a connection;
- - changing the packet size in accordance with the change in the level of interference on the line;
- - dynamic change in transmission rate in accordance with the level of line interference.
Protocol Support V.44 (data compression). The transmitting modem monitors the data flow and, if the data is compressible, compresses and then transmits it through the bottleneck - the telephone network in an already packed form. The receiving modem decompresses the data on the fly and transfers it to the computer. Different types of data are compressed differently: some files are already compressed, such as .zip archives, image files (.gif), .exe, .pdf files. In other cases, for example, in the case of transferring text files or files with HTML code, "modem" compression allows you to get a gain of several percent up to 5-10 times compared to transferring data in its original (uncompressed) form.
One of the advantages of the V.44 protocol is that the bandwidth of the data transmission channel reaches 300 Kbps, which is slightly more than the corresponding characteristic of the previous V.42bis protocol. The V.44 protocol uses lossless compression technologies used in archivers that work according to the Lempel-Ziv algorithm, discussed in paragraph 2.8.
Modem connection
All work on connecting additional devices to the computer is best done by first disconnecting the network cable from the outlet. If the user modem is internal, then, depending on the type, it must be installed in the appropriate slot on the computer motherboard. If the modem is external, then using the appropriate cable, it must be connected either to the serial port or, depending on the type of modem, to the computer's USB port. After that, using a telephone cable (usually included in the kit), you need to connect the modem to the telephone socket, and the telephone to the modem. In order not to be mistaken, you should carefully study the marking of the sockets on the modem itself. As a rule, the jack for connecting the modem to the telephone line is marked "LINE" (line). The other jack is labeled "PHONE" (telephone) and can be plugged into a phone jack.

Rice. 73.
As a rule, a special cable with an RJ11 connector is supplied with the modem to connect the modem to a telephone line. It should be noted that such a connector does not fit standard telephone sockets used in Russia. In addition, it has four lines, while an ordinary city telephone line has only two, so a special adapter is needed to connect the modem to the line (see Fig. 73).
The adapter can be made independently from the cable included in the modem kit and a standard plug/socket telephone set.
For this you need:
- - carefully divide the cable into two equal parts and clean their ends from the braid for a length of 3-4 cm;
- - separate the red and green wires and clean them from the insulation to a length of 1.5 - 2 cm;
- - unused conductors must be shortened and insulated;
- - stripped conductors must be connected to a telephone plug/socket in accordance with the one shown in fig. 74 scheme.
Thus, at connecting an external modem you can follow the following sequence of actions:
- - to determine a rational option for placing a computer, modem, telephone, external modem power supply at the workplace;
- - disconnect the computer from the network and ensure its reliable grounding;
- - connect the connecting cable to the modem and the corresponding serial port of the computer and fasten it to the case with screws;
- - connect the telephone cable to the modem jack labeled "LINE". Insert the telephone plug into the telephone socket;
- - to the modem jack labeled "PHONE" connect the cable ending with a telephone socket to which you want to connect a telephone set;
- - install the modem switches in accordance with the instructions;
- - at a distance of 30 - 40 cm from the computer case, fix the telephone wire harness on the wall or table leg;
- - connect an external power supply to the modem.

Rice. 74.
When installing an internal modem It is useful to follow the following sequence of actions:
- - disconnect the computer from the AC mains by pulling the plug out of the socket;
- - remove the computer cover;
- - choose one of the free slots on the motherboard;
- - remove the protective bar from the back of the computer case opposite the selected slot;
- - install the modem board in the selected slot and make sure that the board is fully inserted into the slot of the computer motherboard;
- - fix the modem board with a screw screwed into the back wall of the computer case;
- - Replace the cover and fasten it with screws.
All modern modems support Plug-and-Play technology (plug and play), that is, they are self-configuring. Therefore, when booting up, the computer itself will detect a new device and try to install it on its own or under the guidance of a user.
Connecting a USB modem
USB modem - a device that connects to the USB port of a computer to connect to the Internet. Consider connecting a USB modem using the Beeline modem as an example. After connecting the modem to the USB port of the computer, the user should use the Setup.exe file, the icon of which is located in the Beeline Internet at Home folder.
It is enough to install the SIM card, which is included in the kit, into the new modem and connect it to the USB port of the computer. The Beeline USB modem program will automatically install on your computer and set up an Internet connection.
Advantages USB modems:
- - there is no need to conclude an agreement with an Internet provider. Wireless Internet will be everywhere where there is a network, for example, Beeline or MTS;
- - no need to call a specialist and wait for connection;
- - ease of installation - the modem requires almost no installation steps;
- - speed - the modem works both in the GSM network (Global System for Mobile Communications - Global System for Mobile Communications) and in the 3G network (Third Generation Wireless - third-generation wireless technologies). Data transmission via GSM can reach 236 Kbps, in a 3G network - 3.6 Mbps.
After the installation wizard dialog box appears (Fig. 75), click the button Further and agree to the terms of the license agreement.
In order to connect to the Internet, just select the menu Start/Connect/WeeIpe or click the "Connect" button located on the Desktop.

Rice.

Rice.
Further Installation Wizard prompts you to select a folder to install the program. After pressing the button Further wait a few seconds for the program to install the program files on your computer. The result of the installation process will be the appearance of a dialog box (Fig. 76), indicating the successful completion of the installation of the program.
Creating an e-mail box and configuring its settings
Before learning how to create an e-mail box, let's look at some terms related to sending and receiving e-mail.
E-mail (E-mail)- this is the name of the service and the service provided for sending and receiving electronic messages over the global computer network.
When we send an email, it is transmitted using the protocol SMTP (Simple Mail Transfer Protocol)- Simple Email Protocol, which is the Internet's standard protocol for sending and receiving email.
The post office protocol is used to receive messages - POP (Post Office Protocol). A protocol similar to POP is called IMAP (Internet Message Access Protocol)- Protocol for accessing Internet e-mail. It provides additional features, such as the ability to search by keyword without storing mail in local memory, but is rarely used. To receive our messages, the mail program installed on the computer connects to the POP server, while the user must enter a login (username) and password.
The email address is written according to the rule Username@domainname, eg This e-mail address is being protected from spambots. You need JavaScript enabled to view it
There are many providers on the Internet that offer free mail services. Of these, mail.ru, yandex.ru, rambler.ru can be distinguished. The process of creating a mailbox on different mail services is actually the same. You just need to go to the website of the provider providing such services, find a link to the registration page and fill out a simple form. After registration, you should remember the login and password for the mailbox, as well as other registration data, such as a security question.
As an example, let's create our own mailbox on the mail.ru service. To do this, go to the site itself at www.mail.ru and click on the link Registration by mail(Fig. 77).

Particular attention should be paid to what name your e-mail box will have, as well as to correctly compose a password. The name must be correct, it is highly undesirable to include the year of your birth, the name of a pet, diminutive names, etc. in it.
Let's not forget that we have to communicate via e-mail not only with our friends, but also indicate the name of our mailbox
on business cards, in business papers, in a resume, when communicating with employers, so it should not be frivolous. It is best if it contains your initials and last name. The registration system will tell you which mailbox name is already taken, or offer possible options.
The password, of course, must be reliable, it is unacceptable to indicate known combinations of characters on the keyboard, for example qwerty, etc., proper names, city names, animal names, etc., i.e. everything that can directly associate with you and relate directly to you.
It is best to use a combination of letters and numbers, and in different registers. You can use the following method: as a password, specify a word or (which is better - a phrase or a short sentence). For example, “let's take” the word “student”, but, having previously switched to the English keyboard layout, we write it down as a password already with the characters next to it on the keyboard along the right diagonal. Then it turns out "fjp67j". Such a password will not only be easy to remember, but also hard to pick up by attackers.
So, we fill out the questionnaire, a similar situation is shown in Fig. 78.

Rice. 78.
Check boxes in Create a personal page on My This e-mail address is being protected from spambots. You need JavaScript enabled to view it and Install Mail.ru Agent may not be installed. It remains to enter the code indicated by the program, confirm it, and this completes the registration process.
The user gets to his mailbox, where the first letter is waiting for him Welcome to Mail.ru content like this:
You have become a user of the largest and most reliable mail service in Runet.
From today at your disposal:
- - unlimited mailbox size;
- - security of correspondence, protection against spam and viruses; - forwarding up to 20 gigabytes with a letter;
- - instant communication with contacts through the Web-Agent in the mail;
- - built-in spell checker, translator from foreign languages;
- - beautiful design of the letter in your style.
The settings will be described in relation to the mail.ru mail service, and since there are quite a lot of them, we will focus on the most important ones.
To change your mailbox settings, click on the link Settings(mailbox must be open). The window shown in Fig. 79.
Letter Master- in this section, you can change the name in the signature to your mailbox, set up forwarding, automatic signature text for the letters you send, autoresponder.

Rice.
Notifications- you can receive notifications about new mail received at your address in the Mail.ru mail system, to any email address, to your mobile phone and personal computer.
Password- You can change your current password at any time. It is recommended that you change your password periodically to improve security.
Password recovery data- if for some reason you forget or lose your password, you will have to recover it using the password recovery system at http://win.mail.ru/cgi-bin/passremind. However, when restoring the system, you may need the following data:
- - secret question and answer to it;
- - additional email address;
- - mobile phone.
Thus, in this section, some data for password recovery is specified in advance.
Security- several options in this section will increase the security level of your mailbox:
- - disable saving login- the server will not remember and automatically substitute your account name on the login page of the mail system;
- - Prohibit parallel sessions- Mail.ru server will detect two or more concurrent users under the same login. If this happens, the server will block the earlier session;
- - show last login information- will allow you to find out when and from which IP address your mailbox was last accessed.
Black list- designed to "cut off" the flow of unwanted letters to your mailbox, i.e. you can pre-compile a list of correspondents from whom you do not want to receive email.
Mail Collector- if you have several email addresses, then you should specify the mail servers from which you want to pick up incoming letters, and the Mail.ru postal service will deliver them to your mailbox.
More detailed information about the operation of the mail program can be found in the Information Center of the Mail.ru mail system at http://www.mail.ru/pages/help/index.html.
And in conclusion, it is worth noting that you should always correctly exit the mail program, namely, be sure to press the button Output. This must be done primarily so that outsiders cannot access your email.
Building an address book
A user who is actively working with e-mail will certainly want to create his own address book, which (in purpose) will be similar to a regular notebook in which we store the addresses of people we know. So, while in the mailbox, click on the tab Addresses, which will allow you to go to the address book page on the Mail.ru service (Fig. 80).

Rice. 80.

Rice. 81. Address Book Settings Rice. 82. Quick add option
All addresses you send emails to are automatically saved to your address book. This feature can be disabled in the address book settings by unchecking the box. Auto add contacts. The addresses that the mail program remembered can be viewed by clicking on the link Everything.
To add a contact, use the option Quick add(Fig. 82), writing down the data of the future addressee in the appropriate fields. Field "E- mail" is mandatory. Three characters cannot be used in the "Nickname" field: """, """ and "" (nicknames for different recipients may be the same).
Write a letter for those people whose addresses you have previously entered in the address book, there are two ways: from the page for writing a letter or from the pages of the address book - just click on the address and select the link Write.
In order to send a postcard to a contact, check the box next to the selected contacts and click the link Send a postcard. You will be taken to the postcard selection page (Fig. 83).

To delete contact from your address book, while in your mailbox, go to the tab Addresses. You will be taken to a page with a list of your correspondents' addresses. Highlight the corresponding contacts in the list and click the link Delete above or below the contact list.
In order to print address book, click on the button *3* above the contact list. A new window will open in front of you, in which the list of contacts will be drawn up on the form of the Mail.ru postal service.
Control questions and tasks
- 1. What is the purpose of the modem?
- 2. List and describe the main characteristics of the modem.
- 3. Name the main types of protocols that modern modems support.
- 4. What innovations does the V.92 protocol support?
- 5. What is meant by error correction?
- 6. What is the purpose of the V.44 protocol?
- 7. How to connect the modem to the telephone line?
- 8. List the sequence of actions required to connect an external modem.
- 9. Name the sequence of actions required to connect the internal modem.
- 10. What are the benefits of USB modems?
- 11. What protocols are used to send and receive e-mail?
- 12. What is the rule for generating an email address? Give an example.
- 13. Register your own mailbox on the Mail.ru service. Describe the registration process with screenshots showing your actions. Send the result to the instructor's email.
- 14. What mailbox settings are available to the user on the Mail.ru service? Explain their purpose.
- 15. How is the formation of the address book?
A well-thought-out and professionally designed network system is required for the full operation of a modern office. This multifunctional network system is designed to transmit various data - from telephone to multimedia, from analog to digital.
Professional design and installation of a computer network is the key to stable and high-quality work. It is important that at each stage of the project, work is carried out in strict accordance with the design standards for structured cabling systems (SCS) and computer local area networks (LANs).
SCS is a complex hierarchical cabling system that is used in a single building or group of buildings. SCS consists of many elements (for example, copper and optical cables, connectors, modular jacks) and auxiliary equipment. Each cable system is divided into subsystems. And each subsystem performs a specific function. Such a structural system is easier to work with, it provides quick access to the necessary objects.
A big plus of cable or wired systems is their versatility. Their design takes into account the principle of open architecture, which allows us to discover new opportunities and flexibly respond to the needs of the organization. And for the client, this means - the rapid equipping of workplaces, without disturbing the rhythm of the entire enterprise.
Wired networks are a high privacy system that requires professional maintenance. So far, one of the disadvantages of wired networks is the need for installation work. This leads to "attachment" to the workplace and lack of mobility.
The complexity of installing and configuring a wireless network is obvious and therefore it must be trusted to the specialists who work in our company.
Wired local area networks are the basis of any computer network and can turn a computer into a very flexible and versatile tool, without which modern business is simply impossible.
The local network allows ultra-fast data transfer between computers, working with any database, collective access to the Internet, working with e-mail, printing information on paper using only one print server, and much more that optimizes the workflow, and thereby increasing the efficiency of the company.
It is also important that the specialists of Support Good Quality are able to perform all the work necessary to organize a proper security policy in the field of a local computer network, create effective anti-virus protection and take care of excluding the possibility of unauthorized access from outside (the global Internet).
Wireless LANs
Obtaining high results and achievements in the field of modern technologies made it possible to supplement local networks with "wireless" technologies. In other words, wireless networks that operate on the exchange of radio waves can be a wonderful addition to any part of a wired network. Their main feature is that in places where the architectural elements of the premises or building in which the company or organization is located do not provide a cable network, radio waves can cope with the task.
Wireless LANs are becoming more and more popular among users. Within a few years they have been improved, the speed has been increased, the prices have become more affordable.
Today, wireless networks allow users to provide connectivity where cable connections are difficult or complete mobility is required. At the same time, wireless networks interact with wired networks. Nowadays, wireless solutions must be taken into account when designing any network - from a small office to an enterprise. This will help you save money, time and labor.
WI-FI is a modern wireless technology for transmitting data over a radio channel (wireless, wlan)
WiFi Benefits:
No wires.
Data transmission over the network is carried out over the "air" at very high frequencies, which do not affect and do not cause electronic interference and harm to human health.
Mobility.
Since the wireless network is not connected by wires, you can change the location of your computer within the range of the access point without worrying about communication disruptions. The network is easy to assemble and disassemble. When moving to another location, you can even take your network with you.
Technology uniqueness.
Installation is possible in places where installation of a wired network is impossible or impractical, in places such as exhibitions, conference rooms.
Disadvantages of WiFi:
Relatively high cost of equipment. The speed depends on the transmission medium.
Although modern technology allows you to reach speeds up to 108 Mb / s, which is comparable to the speed of cable networks, the speed depends on the signal transmission medium.
To improve the signal quality, you can benefit from installing an additional external antenna: narrowly directional for line-of-sight connections, or so that the signal propagates in one direction and omnidirectional when you need to increase coverage indoors.
Wireless Network Security.
Currently, Wi-Fi equipment is used, which is equipped with a set of security equipment and professional settings, allowing you to achieve almost 100% wireless network security guarantee.
However, wireless networks are only an additional element of the local network, where the main work falls on the main cable for data exchange. The main reason for this is the phenomenal reliability of the wired LAN, used by all modern companies and organizations, regardless of their size and employment.
The installation of networks carried out by the specialists of Support Good Quality is carried out taking into account all the necessary international norms and standards, which is a reliable guarantee of the quality and performance of networks and computers connected to it.
Wireless data transmission (wireless communication) is communication that bypasses wires or other physical transmission media. For example, the Bluetooth wireless data transfer protocol works "over the air" over a short distance; NFC may come to replace it. Wi-Fi is another way to transfer data (internet) over the air. Cellular also refers to wireless. Although wireless communication protocols are improving year by year, they still do not bypass wired communication in terms of their basic indicators and transmission speed. Although the LTE network and its newest iterations show great promise in this field.
Today you will not surprise anyone with wireless data transmission. Moreover, few people are surprised by the fast data transfer over vast distances. Having contacted a friend from anywhere in the world in any more or less advanced messenger, we can transfer photos, videos, documents, or simply write a message, and our friend will receive this information almost instantly. All this is possible thanks to an extensive network of radio communication towers, repeaters, access points and more. It seemed to a group of researchers from Japan that this was not enough, and not so long ago they presented a device thanks to which it is possible to transfer data over vast distances directly between devices, without the participation of "intermediate links".